In the dynamic landscape of smart contracts and decentralized applications (dApps), security takes center stage. While the intricate logic of on-chain code often garners significant attention, the critical aspect of framework security can be inadvertently overlooked. This oversight can have dire consequences, as vulnerabilities in the underlying framework or language can expose dApps to significant risks.
A poignant example of the devastating impact of inadequate framework security is the infamous Wormhole hack of 2022, which resulted in a staggering loss of $350 million. This incident serves as a stark reminder that neglecting framework security can have catastrophic financial implications, even for well-established projects.
The Wormhole Hack: A Case Study in Framework Vulnerability
The Wormhole protocol, designed to enable the seamless transfer of assets between different blockchains, fell victim to a critical vulnerability in its Solana implementation. At the heart of this exploit was the use of an insecure and deprecated function, load_instruction_at, in an outdated version of the Solana framework. This function was meant to verify the authenticity of sysvar accounts, which are hardcoded addresses used to access specific state data on the Solana blockchain.
However, the vulnerability in load_instruction_at allowed attackers to spoof arbitrary addresses as legitimate sysvar accounts, bypassing the intended security checks. Wormhole’s reliance on this flawed function to verify user permissions for minting wrapped Ethereum (WETH) on the Solana blockchain provided an opening for the attackers to drain the protocol’s WETH collateral.
Adding to the severity of the situation was the way the Wormhole team handled the security patch. While they had identified the vulnerability and committed a fix to their public GitHub repository, the patch was not immediately deployed to the production environment. This delay, albeit unintentional, gave attackers a window of opportunity to exploit the vulnerability before it was addressed on-chain.
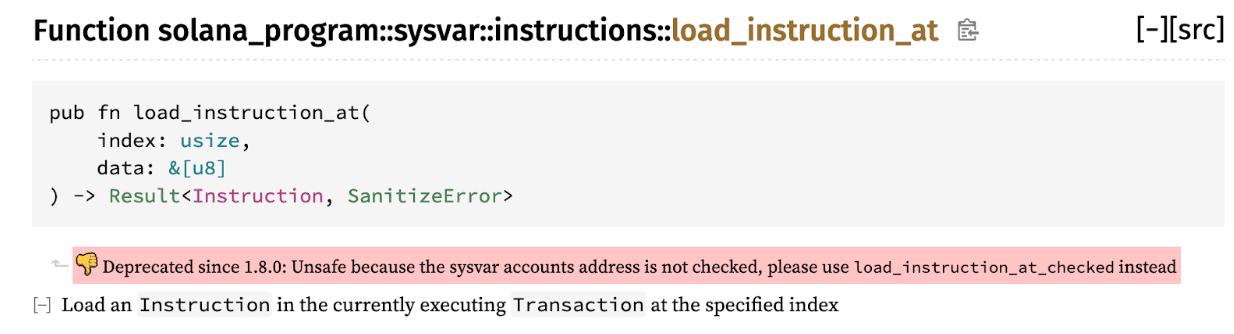
Figure 1: The load_instruction_at function was deprecated after Solana version 1.7.0
The Importance of Silent Patching in Decentralized Ecosystems
The Wormhole incident highlights the need for a more robust approach to handling security-critical updates, particularly in decentralized ecosystems where resources are often outside the direct control of developers. Silent patching, a strategy employed by projects like Go Ethereum (geth), offers a balanced approach to security and transparency.
Under the silent patching model, a fix for a critical vulnerability is first developed and deployed to production without fanfare. This is followed by a period of delay, typically several weeks, before disclosing the existence of the security update. Finally, the details of the vulnerability are publicly disclosed, giving users and developers ample time to update their systems.
This approach helps mitigate the risk of attackers exploiting vulnerabilities before users can apply necessary patches. By initially keeping the vulnerability under wraps, silent patching buys time for the ecosystem to adopt the fix, thereby minimizing potential damage.
Mitigating Framework Security Risks: Best Practices for Developers
Preventing framework-related security breaches requires a proactive and multi-faceted approach. Developers should prioritize the following best practices:
- Stay Up-to-Date: Use the latest stable versions of development frameworks, libraries, and languages. Regularly update dependencies to ensure you benefit from the latest security enhancements.
- Heed Deprecation Warnings: Pay close attention to deprecation warnings during compilation and while reviewing documentation. These warnings often signal potential security risks associated with outdated functions or methods.
- Consult Known Vulnerability Databases: Leverage resources like the Solidity compiler’s list of known bugs to cross-reference against the versions you’re using. This helps uncover potential vulnerabilities that might have been missed during initial reviews.
- Practice Secure Development Principles: Implement robust security measures throughout the development lifecycle, including code review, static analysis, and thorough testing.
- Foster a Culture of Security: Encourage open communication about security issues and promote continuous learning and improvement within your team.

Figure 2: The crucial security update was bundled with numerous other changes in a single commit.
The Way Forward: Fostering a More Secure Web3 Ecosystem
The Wormhole hack serves as a sobering reminder that framework security is an indispensable aspect of building secure and resilient dApps. While individual developers and projects bear the responsibility of implementing robust security measures, fostering a more secure Web3 ecosystem requires a collective effort.
Projects developing core blockchain infrastructure and languages have a critical role to play in promoting transparency, responsible disclosure, and timely security updates. By embracing best practices like silent patching and proactively communicating potential risks to the community, we can collectively work towards a more secure and trustworthy Web3 future.

